The Deepest Reorg in Blockchain History
with ANTOINE LE CALVEZ
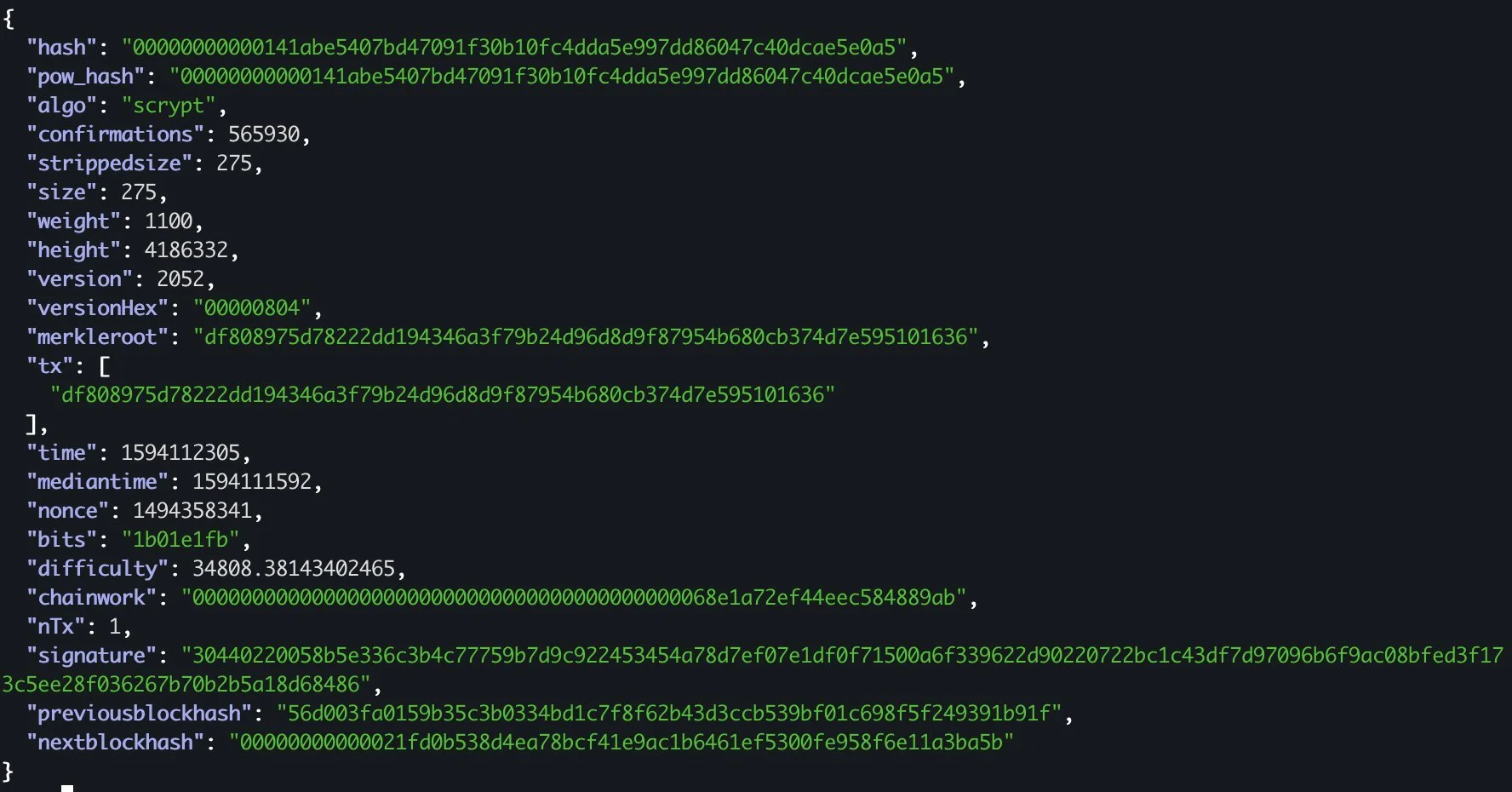
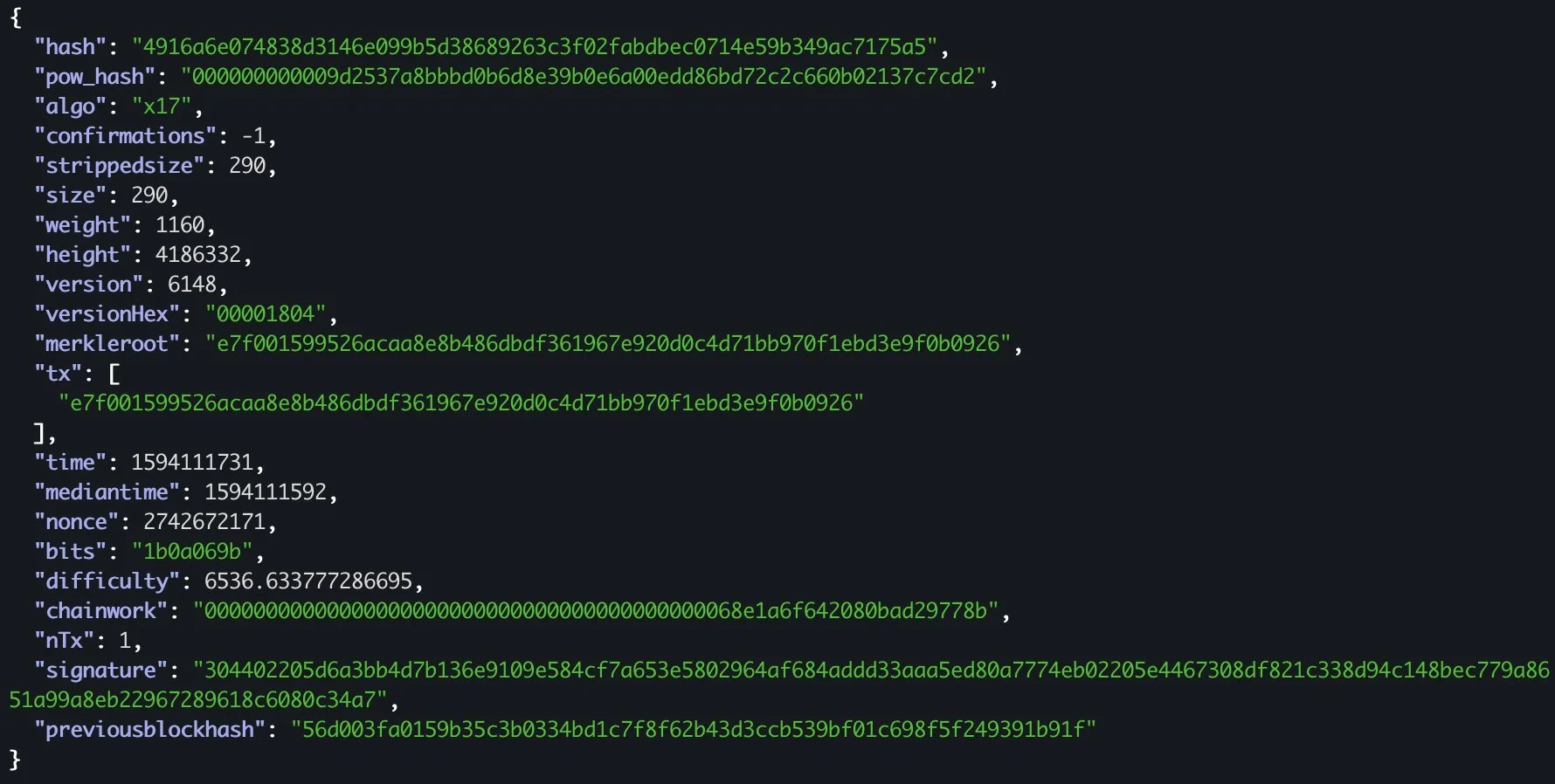
On Feb. 15, 2021 we identified what we considered to be the deepest reorg to ever happen in a “established” blockchain. It all started when our Verge (XVG) node at Coin Metrics began downloading a huge number of previously unknown blocks. Once downloaded, these blocks led to a massive block reorganization (reorg) event, involving over 560,000 blocks. Put simply, around 200 days worth of previously-confirmed transaction history simply vanished. To our knowledge, this was by far the deepest reorg in a cryptocurrency within the top 100.
A snapshot of the XVG blockchain prior to the reorg.
The snapshot of the chain after the reorg.
This was no “vanilla” 51% attack. The mining rewards alone received by the attacker amounted to over 58M USD. If the attacker also “double-spent” funds, the potential payout could have been a lot higher.
So how did it happen?
The first thing to consider is that Verge can be mined with 5 different algorithms; Scrypt, X17, Lyra2rev2, MYR groestl, and Blake2S. This has become a big no-no in blockchain security because it makes it more challenging to build a robust difficulty adjustment algorithms that are responsive to big inflows and outflows of hashrate. The attacker likely exploited one the five algorithms to produce a chain with more accumulated work, which, as per Nakamoto Consensus, makes that chain the “valid” one.
What’s more, in order to go back in time about 200 days, the attacker also manipulated timestamps to make the difficulty adjustment algorithm malfunction. Unlike Bitcoin, Verge had no notion of “consensus time” implemented, which is a protection mechanism that normalizes block timestamps. This, combined with not one but five niche mining algorithms, created (in retrospect) some pretty obvious attack vectors.
Verge’s response to this was to send out a “checkpoint” as a hard fork that restored the previous version of the chain and invalidated the attacker’s reorg. By then, however, there was plenty of time for the attacker to cash out and carry out double spend attacks. Furthermore, by forcing the addition of checkpointing to the Verge node client, the project also inadvertently added yet another attack vector (for a DDoS) and a centralization factor (the “dictator” of the checkpoint itself).
Our disclosure and research around the attack was covered by CryptoBriefing and Bitcoin.com News.